IEEE 802.1X is an IEEE Standard for port-based Network Access Control to prevent unauthorized devices from gaining access to the network. It defines the encapsulation of the Extensible Authentication Protocol (EAP) over IEEE 802, known as “EAP over LAN” or EAPOL.
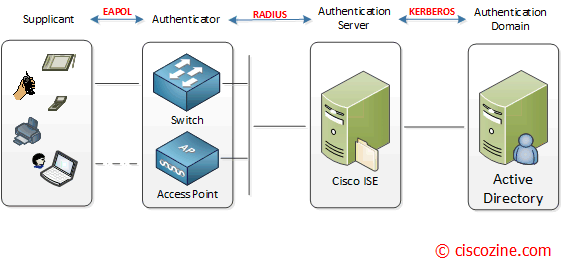
802.1X authentication involves three parties: a supplicant, an authenticator, and an authentication server.
- The supplicant is a client device (such as a laptop) that wishes to attach to the LAN/WLAN.
- The authenticator is a network device which provides a data link between the client and the network and can allow or block network traffic between the two, such as an switch or access point.
- The authentication server is a trusted server (for instance Cisco Identity Services Engine) that receive and respond to requests for network access, and can decide if the connection is to be allowed or not.
Remember: EAP is always carried by another protocol.
The most common transports between the supplicant and the authenticator is EAPOL. For the link between the authenticator and the authentication server, the EAP packets are fragmented on 253-byte boundaries and split into multiple EAP-Message attributes. How EAP is transported over RADIUS is defined by RFC3579.
There are many EAP types, and each one has its own benefit and downside.
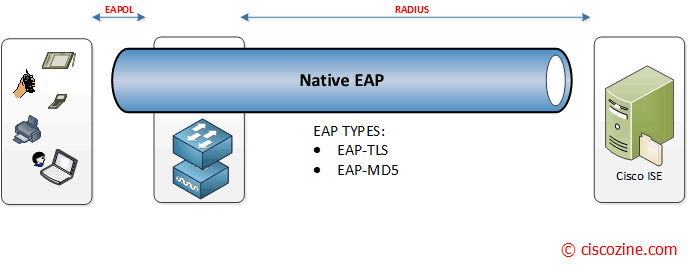
The EAP types can be broken down into two categories: native EAP types and tunneled EAP types.
Native EAP (nontunneled EAP): EAP-TLS, EAP-MD5.
- EAP-TLS: it provides the secure identity transaction. This is very similar to SSL and the way encryption is formed between your web browser and a secure website. EAP-TLS has the benefit of being an open IETF standard, and is considered “universally supported“. EAP-TLS uses X.509 certificates and provides the ability to support mutual authentication, where the client must trust the server’s certificate, and vice-versa. It is considered among the most secure EAP Types, since password capture is not an option.
- EAP-MD5: it verifies MD5 hash of a user password for authentication. This method is not more used due to the MD5 weaknesses.
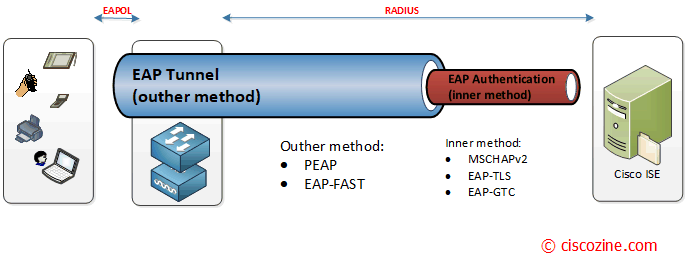
Tunneled EAP – Outer method: PEAP, EAP-FAST.
- PEAP aka Protected EAP: Originally proposed by Microsoft, this EAP Tunnel type has quickly become the most popular and widely deployed EAP method in the world. PEAP will form a potentially encrypted TLS tunnel between the client and server, using the x.509 certificate on the server in much the same way the SSL tunnel is established between a web browser and a secure website. After the tunnel has been formed, PEAP will use another EAP type as an “inner method” – authenticating the client using EAP within the outer tunnel.
Note: PEAP requires only a server-side PKI certificate to create a secure TLS tunnel. - EAP-FAST: Flexible Authentication via Secure Tunnel (FAST) is very similar to PEAP. FAST was created by Cisco as an alternative to PEAP that allows for faster re-authentications and supports faster wireless roaming. Just like PEAP, FAST forms a TLS outer-tunnel and then transmits the client credentials within that TLS tunnel.
Tunneled EAP – Inner method: EAP-GTC, EAP-TLS, EAP-MSCHAPv2.
- EAP-GTC (Generic Token Card): it uses clear text method to exchange authentication controls between the client and the server. Since the authentication mechanism uses the one-time tokens (generated by the card), this method of credential exchange is considered safe. In addition, EAP-GTC is used in PEAP or TTLS tunnels in wireless environments.
- EAP-TLS: it is rarely used and not widely known; PEAP is capable of using EAP-TLS as an inner method.
- EAP-MSCHAPv2: the client’s credentials are sent to the server encrypted within an MSCHAPv2 session. This is the most common inner-method, as it allows for simply transmission of username and password, or even computer name and computer passwords to the RADIUS server, which in turn authenticates them to Active Directory.
Note: There are currently about 40 different methods, but these ones are the most common used.
Remember: Not all the network devices support 802.1X, such as a printer, camera, or a wireless phone. Such devices lack the supplicant feature which is needed to pass on the 802.1X authentication credentials between the client and the authentication server. In this case, you can use MAC Authentication Bypass (MAB) function to authenticate network devices.
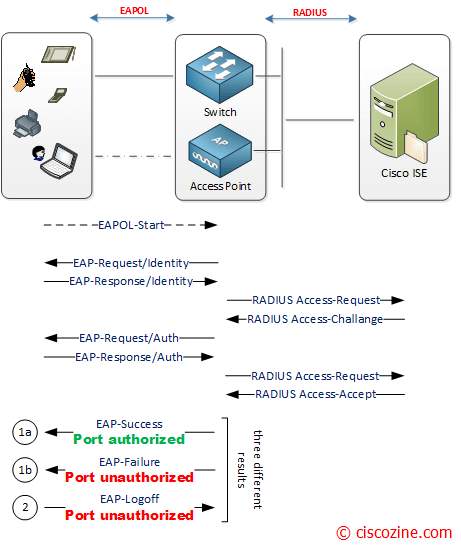
In the figure below the authentication process and message exchange.
During bootup, if the supplicant does not receive EAP-Request/Identity message from the authenticator, the supplicant initiates authentication by sending the EAPOL-Start frame, which prompts the authenticator to request the supplicant’s identity.
Then the identity and authentication process starts between the suppplicant/authenticator and the authenticator/authentication server.
If the identity/authentication process goes fine, an EAP-Success packet is sent back to the client and the port is authorized (1.a).
If the identity/authentication process fails for any reason (for instance wrong username or password, certificate expired, …) an EAP-Failure packet should be sent instead and the port is unauthorized (1.b).
Note: When the supplicant wants to log off, an EAPOL-Logoff message can be sent to unauthorize the port (2).
References: