Network address translation (NAT) is the process of modifying IP address information in IP packet headers while in transit across a traffic routing device.
There are two different types of NAT:
- NAT
- Static NAT: The simplest type of NAT provides a one-to-one translation of IP addresses. It is often also referred to as one-to-one NAT. In this type of NAT only the IP addresses, IP header checksum and any higher level checksums that include the IP address need to be changed. The rest of the packet can be left untouched (at least for basic TCP/UDP functionality, some higher level protocols may need further translation). Basic NATs can be used when there is a requirement to interconnect two IP networks with incompatible addressing. With static NAT, translations exist in the NAT translation table as soon as you configure static NAT command(s), and they remain in the translation table until you delete the static NAT command(s).
- Dynamic NAT: Dynamic NAT has some similarities and differences compared to static NAT. Like static NAT, the NAT router creates a one-to-one mapping between an inside local and inside global address and changes the IP addresses in packets as they exit and enter the inside network. However, the mapping of an inside local address to an inside global address happens dynamically. Dynamic NAT sets up a pool of possible inside global addresses and defines matching criteria to determine which inside local IP addresses should be translated with NAT. The dynamic entry stays in the table as long as traffic flows occasionally. With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation. Dynamic translations have a timeout period after which they are purged from the translation table.
- PAT
- Static PAT: Static PAT translations allow a specific UDP or TCP port on a global address to be translated to a specific port on a local address. Static PAT is the same as static NAT, except that it enables you to specify the protocol (TCP or UDP) and port for the real and mapped addresses. Static PAT enables you to identify the same mapped address across many different static statements, provided that the port is different for each statement. You cannot use the same mapped address for multiple static NAT statements. With static PAT, translations exist in the NAT translation table as soon as you configure static PAT command(s), and they remain in the translation table until you delete the static PAT command(s).
- NAT Overload or PAT: It is common to hide an entire IP address space, usually consisting of private IP addresses, behind a single IP address (or in some cases a small group of IP addresses) in another (usually public) address space. This type of NAT is called PAT in overload. The dynamic entry stays in the table as long as traffic flows occasionally. With PAT in overload, translations do not exist in the NAT table until the router receives traffic that requires translation. Translations have a timeout period after which they are purged from the translation table.
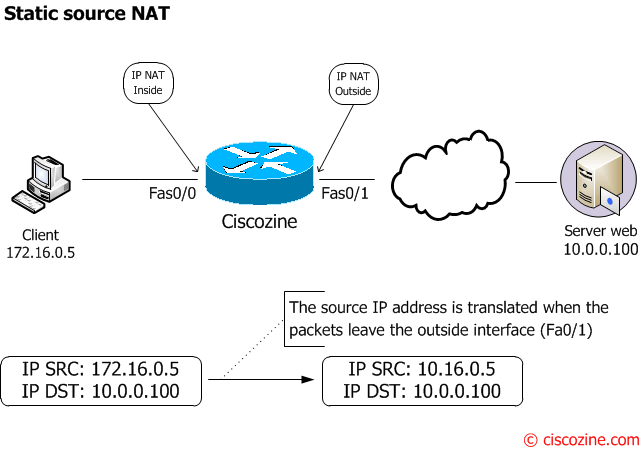
Example #1: Static Source NAT
How to translate the 172.16.0.5 IP address to the 10.16.0.5 ip address.
Define the ip nat inside:
Ciscozine(config)#interface fa0/0 Ciscozine(config-if)#ip nat inside
Define the ip nat outside:
Ciscozine(config)#interface fa0/1 Ciscozine(config-if)#ip nat outside
Define the static NAT entry:
ip nat inside source static 172.16.0.5 10.16.0.5
With static NAT, translation exists in the NAT translation table as soon as you configure static NAT command, and it remains in the translation table until you delete the static NAT command:
Ciscozine#sh ip nat translations Pro Inside global Inside local Outside local Outside global --- 10.16.0.5 172.16.0.5 --- --- Ciscozine#
If the client sends an ICMP packet or an HTTP request to the web server, the nat table will be:
Ciscozine#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 10.16.0.5:1 172.16.0.5:1 10.0.0.100:1 10.0.0.100:1 tcp 10.16.0.5:56080 172.16.0.5:56080 10.0.0.100:80 10.0.0.100:80 --- 10.16.0.5 172.16.0.5 --- --- Ciscozine#
Remember: Because the mapped address is the same for each consecutive connection with static NAT, and a persistent translation rule exists, static NAT allows hosts on the destination network to initiate traffic to a translated host (if an access list exists that allows it).
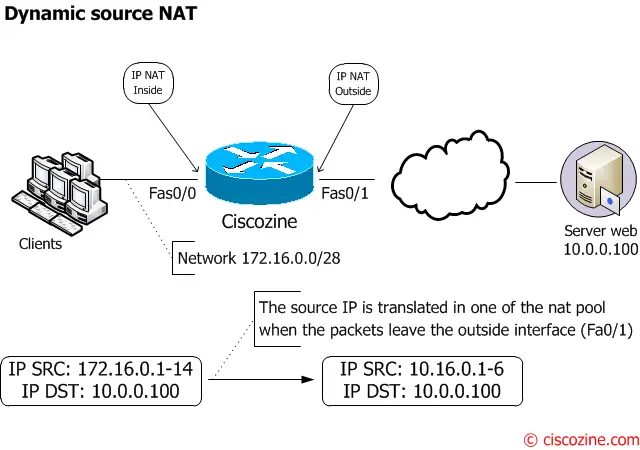
Example #2: Dynamic Source NAT
How to translate the 172.16.0.0/28 network in the 10.16.0.0/29 network.
Define the ip nat inside:
Ciscozine(config)#interface fa0/0 Ciscozine(config-if)#ip nat inside
Define the ip nat outside:
Ciscozine(config)#interface fa0/1 Ciscozine(config-if)#ip nat outside
Define the nat pool used in the NAT translation:
Ciscozine(config)#ip nat pool dynamic-ip 10.0.16.1 10.0.16.6 prefix-length 29
Define which network will be translated:
Ciscozine(config)#ip access-list standard client-list Ciscozine(config-std-nacl)#permit 172.16.0.0 0.0.0.15
Define the dynamic source NAT:
Ciscozine(config)#ip nat inside source list client-list pool dynamic-ip
With dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation.
Ciscozine#sh ip nat translations Ciscozine#
but when some packets match the ACL..
Ciscozine#sh ip nat translations Pro Inside global Inside local Outside local Outside global icmp 10.0.16.1:2 172.16.0.1:2 10.0.0.100:2 10.0.0.100:2 tcp 10.0.16.2:35694 172.16.0.2:35694 10.0.0.100:80 10.0.0.100:80 tcp 10.0.16.1:56185 172.16.0.1:56185 10.0.0.100:80 10.0.0.100:80 --- 10.0.16.1 172.16.0.1 --- --- --- 10.0.16.2 172.16.0.2 --- --- Ciscozine#
Note: If a new packet arrives from yet another inside host, and it needs a NAT entry, but all the pooled IP addresses are in use, the router simply discards the packet.
This can be checked enabling the “debug ip nat”.
Feb 12 19:26:09.895: NAT: translation failed (E), dropping packet s=172.16.0.5 d=10.0.0.100
The user must try again until a NAT entry times out, at which point the NAT function works for the next host that sends a packet. Essentially, the inside global pool of addresses needs to be as large as the maximum number of concurrent hosts that need to use the Internet at the same time—unless we use PAT.
Remember: The main difference between dynamic NAT and a range of addresses for static NAT is that static NAT allows a remote host to initiate a connection to a translated host (if an access list exists that allows it), while dynamic NAT does not. You also need an equal number of mapped addresses as real addresses with static NAT.
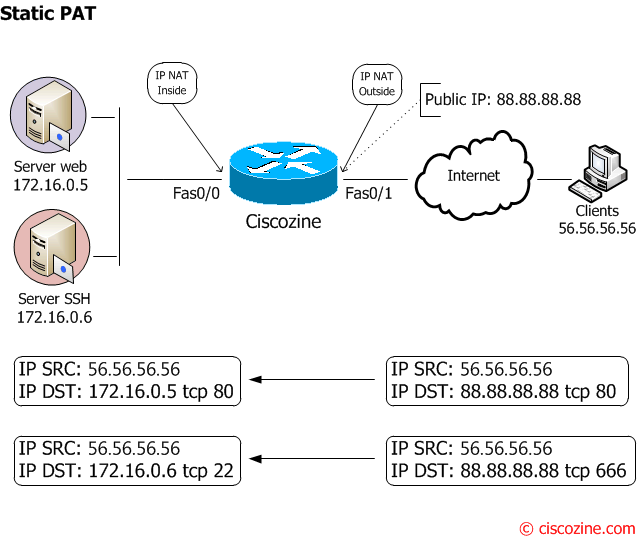
Example #3: Static PAT
How to expose two different services on Internet:
- The Web server (172.16.0.5) is listening on tcp port 80; this server responds on public address 88.88.88.88:80 from the Internet (outside).
- The SSH server (172.16.0.6) is listening on tcp port 22; this server responds on public address 88.88.88.88:666 from the Internet (outside) .
Define the ip nat inside:
Ciscozine(config)#interface fa0/0 Ciscozine(config-if)#ip nat inside
Define the ip nat outside:
Ciscozine(config)#interface fa0/1 Ciscozine(config-if)#ip nat outside
Define the static PAT:
The web server responds on tcp port 80 on the ‘outside’ interface.
ip nat inside source static tcp 172.17.0.5 80 88.88.88.88 80
The SSH server responds on tcp port 666 on the ‘outside’ interface ; in this case, the real port (22 tcp) is translated to the 666 tcp port when a request comes from Internet.
ip nat inside source static tcp 172.17.0.6 22 88.88.88.88 666
Like static NAT, static PAT translation exists in the NAT translation table as soon as you configure static PAT command, and it remains in the translation table until you delete the static PAT command.
Ciscozine#sh ip nat translations Pro Inside global Inside local Outside local Outside global tcp 88.88.88.88:80 172.16.0.5:80 --- --- tcp 88.88.88.88:666 172.16.0.6:22 --- --- Ciscozine#
If an Internet client sends an HTTP request or an SSH Connection (on tcp port 666), the nat table will be:
Ciscozine#sh ip nat translations Pro Inside global Inside local Outside local Outside global tcp 88.88.88.88:80 172.16.0.5:80 56.56.56.56:54686 56.56.56.56:54686 tcp 88.88.88.88:80 172.16.0.5:80 --- --- tcp 88.88.88.88:666 172.16.0.6:22 56.56.56.56:33704 56.56.56.56:33704 tcp 88.88.88.88:666 172.16.0.6:22 --- --- Ciscozine#
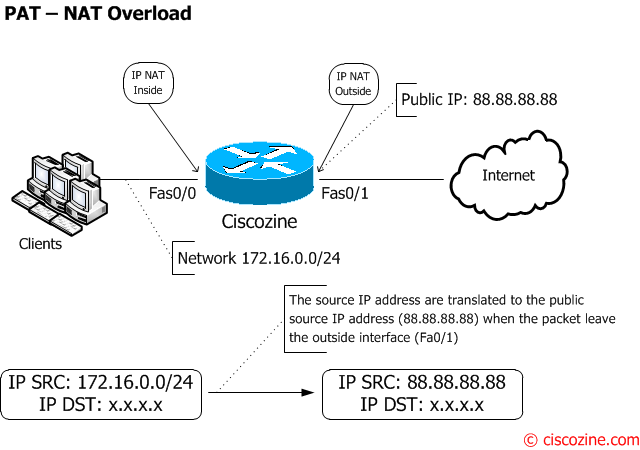
Example #4: PAT – NAT Overload
How to share an Internet connection.
Define the ip nat inside:
Ciscozine(config)#interface fa0/0 Ciscozine(config-if)#ip nat inside
Define the ip nat outside:
Ciscozine(config)#interface fa0/1 Ciscozine(config-if)#ip nat outside
Define which network will be translated:
Ciscozine(config)#ip access-list standard client-list Ciscozine(config-std-nacl)#permit 172.16.0.0 0.0.0.255
Define the NAT Overload:
Ciscozine(config)#ip nat inside source list client-list interface fastethernet0/1 overload
Like dynamic NAT, translations do not exist in the NAT table until the router receives traffic that requires translation:
Ciscozine#sh ip nat translations Ciscozine#
but when some packets match the ACL..
Ciscozine#show ip nat translations Pro Inside global Inside local Outside local Outside global tcp 88.88.88.88:7921 172.16.0.2:7921 95.100.96.233:443 95.100.96.233:443 tcp 88.88.88.88:8651 172.16.0.5:8651 173.194.44.18:80 173.194.44.18:80 tcp 88.88.88.88:8652 172.16.0.111:8652 173.194.44.18:443 173.194.44.18:443 tcp 88.88.88.88:8653 172.16.0.223:8653 173.194.70.84:443 173.194.70.84:443 udp 88.88.88.88:64116 172.16.0.222:64116 8.8.8.8:53 8.8.8.8:53 udp 88.88.88.88:64756 172.16.0.223:64756 8.8.4.4:53 8.8.4.4:53 Ciscozine#
Are there other types of NAT/PAT?
The answer is YES! One type of NAT/PAT widely used is the ip nat outside source; this command permits to translate the source address of a packet that enter in the ‘outside’ interface and leave the ‘inside’ interface.
In simple terms, if you see the first example #1
The command:
ip nat outside source static 10.0.0.100 192.168.0.100
translate the 10.0.0.100 to the 192.168.0.100 , so the client must call the 192.168.0.100 ip address to contact the server web and not the 10.0.0.100.
Another particolar type of nat is the ip nat inside destination used when multiple inside devices are identical servers with mirrored content, which from the outside appear to be a single server load balancing.
You define a pool of addresses containing the real hosts’ addresses ending with “type rotary” making the servers available in round-robin fashion. The access list now permits the IP address of the virtual host, i.e. what the outside world thinks is the host address. So the virtual host is 123.123.123.132, with the real hosts being 172.16.0.2 through 10.
Partial configuration
interface FastEthernet0/0 ip address 172.16.0.0 255.255.255.0 ip nat inside ! interface FastEthernet0/1 ip address 88.88.88.88 255.255.255.252 ip nat outside ! ip nat pool real-ip-server 172.16.0.2 172.16.0.10 prefix-length 24 type rotary ip nat inside destination list 1 pool real-ip-server ! ip route 0.0.0.0 0.0.0.0 FastEthernet0/1 ! access-list 1 permit 123.123.123.123
This translation is not bi-directional in nature. You will have to use a one to one static NAT to accomplish it. A “ip nat inside source static” kind of funtionality can be achieved with the above configuration using a single address in the NAT pool, but that would only work for outside to inside traffic.
Where apply nat inside/outside?
Typically “ip nat inside” is configured on the interfaces in your local environment which cannot be routed to the Internet (typically private range of IP Addresses) and and “ip nat outside” on the interface which is connected to the Internet.
When does the router perform NAT?
Inside to Outside:
- If IPSec then check input access list
- decryption – for CET (Cisco Encryption Technology) or IPSec
- check input access list
- check input rate limits
- input accounting
- redirect to web cache
- policy routing
- routing
- NAT inside to outside (local to global translation)
- crypto (check map and mark for encryption)
- check output access list
- inspect (Context-based Access Control (CBAC))
- TCP intercept
- encryption
- Queueing
Outside to Inside:
- If IPSec then check input access list
- decryption – for CET or IPSec
- check input access list
- check input rate limits
- input accounting
- redirect to web cache
- NAT outside to inside (global to local translation)
- policy routing
- routing
- crypto (check map and mark for encryption)
- check output access list
- inspect CBAC
- TCP intercept
- encryption
- Queueing
Some useful comands:
- To see some statistics about NAT: show ip nat statistics
- To see a complete list of the static/dynamic NAT/PAT entries: show ip nat translations
- To clear dynamic nat entry: clear ip na translation *
- To debug NAT: debug ip nat
References:

Awesome
It is so very nice to see information put into terms that the everyday user can understand. Thank You!
It will be very helpful for new comer…..Thanks.
Awesome indeed.
Many thanks for your time on this document…
Thank you so much for your time on this issue
Very beautiful article.
Helped me a lot in reminding stuffs.
thank you,very helpful for me.
In the first example:
Target:
Convert IP 172.16.0.5 to 10.16.0.5
Command used:
ip nat inside source static 172.16.0.6 10.16.0.5
Why are we converting 172.16.0.6 when the target is to convert 172.16.0.5 ???
really helpfull, thanks for sharing
Thanks for posting, very informative and easy to follow. Especially like the diagrams, they make it really easy to understand.
great post, thank you
Pardon me for my stupid question.
Are not 172.16.0.5 and 10.16.0.5 part of private addresses? If so, then how 10.16.0.5 could be a global address representing 172.16.0.5?
Thanks
Asim Roy
The nat could be used for Internet connection but also for private network.
great one
Great :)
I saw this article 3 years ago.
Somebody confused me. I google and your familiar webpage opens again..
Great and unique article on web :)
You helped so many when many people try to confuse these terms. I think most of them don’t comments and just read your page. Thanks :)
Hello, just a question. Should I configure the router IP addresses for inside local/global interface? In all tutorials thery are never configured…
You can also configure the interface to nat.