On Thursday June 6, 2019, traffic destined to some of Europe’s biggest mobile providers was misdirected in a roundabout path through the Chinese-government-controlled China Telecom, in some cases for more than two hours.
“Swiss data center colocation company AS21217 leaked over 70,000 routes to China Telecom (AS4134) in Frankfurt, Germany. China Telecom then announced these routes on to the global internet redirecting large amounts of internet traffic destined for some of the largest European mobile networks through China Telecom’s network. Impacts were seen by some of Europe’s largest networks in Switzerland, Holland, and France among other countries.” said Doug Madory, Director of Oracle’s Internet Analysis division (formerly Dyn).
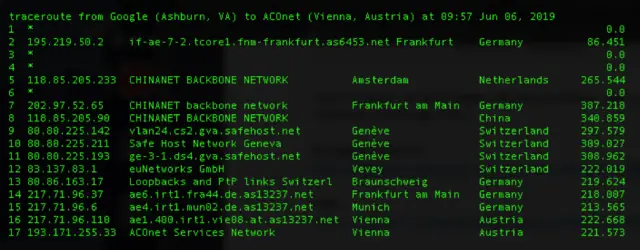
The following traceroute shows traffic starting at a Google Cloud server in Virginia passing through China Telecom’s backbone network before finally reaching its intended IP address located in Vienna, Austria.
“The incident shows that the Internet has not yet eradicated the problem of BGP route leaks. It also reveals that China Telecom, a major International carrier, has still implemented neither the basic routing safeguards necessary both to prevent the propagation of routing leaks nor the processes and procedures necessary to detect and remediate them in a timely manner when they inevitably occur” said Doug Madory.
Experts say BGP leaks, while distressingly common, are also preventable in some cases, and, thankfully, quite visible to the network. In fact, to fix BGP organizations should primarily look to two protocols: Resource Public Key Infrastructure and BGPSec.
The Resource Public Key Infrastructure (RPKI) system is a way to improve routing security by associating an IP address range with an autonomous system number (ASN) through cryptographic signatures, as described in RFC 6480. RPKI leverages X.509 certificates (RFC 5280) with added extentions for IPv4 and IPv6 prefixes, and AS numbers defined in RFC 3779.
RFC 8205 is the BGPSec Protocol Specification that has been published as standard. BGPsec is an extension to the Border Gateway Protocol (BGP) that provides security for the path of autonomous systems (ASes) through which a BGP update message propagates. BGPsec is implemented via an optional non-transitive BGP path attribute called BGPsec_Path, that carries digital signatures produced by each autonomous system propagating the update message. The digital signatures provide confidence that every AS on the path of ASes listed in the update message has explicitly authorized the advertisement of the route.
In any case, BGP route leaks are not without precedent (the last was two days ago with Verizon BGP route leak).
Below the public incidents of the last two years:
- January 2017: Iranian pornography censorship.
- April 2017: Russian telecommunication company Rostelecom (AS12389) originated 37 prefixes for numerous other Autonomous Systems. The hijacked prefixes belonged to financial institutions (most notably MasterCard and Visa), other telecom companies, and a variety of other organizations.
- December 2017: Eighty high-traffic prefixes normally announced by Google, Apple, Facebook, Microsoft, Twitch, NTT Communications, Riot Games, and others, were announced by a Russian AS, DV-LINK-AS (AS39523).
- April 2018: Roughly 1300 IP addresses within Amazon Web Services space, dedicated to Amazon Route 53, were hijacked by eNet (or a customer thereof), an ISP in Columbus, Ohio. Several peering partners, such as Hurricane Electric, blindly propagated the announcements.
- July 2018: Iran Telecommunication Company (AS58224) originated 10 prefixes of Telegram Messenger.
- November 2018: US-based China Telecom site originated Google addresses.
- May 2019: Traffic to a public DNS run by Taiwan Network Information Center (TWNIC) was rerouted to an entity in Brazil (AS268869).
References: