Do you remember the article “How to analyze traffic with SPAN feature“? The SPAN port is a feature that mirror traffic (on physical or virtual port) to a specific port. In general, behind this ‘destination’ port can be a traffic analyzer (wireshark, ntop and so on…), an IDS or other appliances.
The SPAN feature is a good tool but it has two limitations:
- The number of SPAN sessions that can be configured is limited.
- A destination port receives copies of sent and received traffic for all monitored source ports. If a destination port is oversubscribed, it can become congested. This congestion can affect traffic forwarding on one or more of the source ports.
The VACL Capture Port feature can help to overcome some of these limitations. VACLs are primarily not designed to monitor traffic, but, with a wide range of capability to classify the traffic, the Capture Port feature was introduced so that network traffic analysis can become much simpler. These are the advantages of VACL Capture Port usage over SPAN:
- Granular Traffic Analysis: VACLs can match based on source IP address, destination IP address, Layer 4 protocol type, source and destination Layer 4 ports, and other information. This capability makes VACLs very useful for granular traffic identification and filtering.
- Number of Sessions: VACLs are enforced in hardware; the number of Access Control Entries (ACE) that can be created depends upon the TCAM available in the switches.
- Destination Port Oversubscription: Granular traffic identification reduces the number of frames to be forwarded to the destination port and thereby minimizes the probability of their oversubscription.
- Performance: VACLs are enforced in hardware; there is no performance penalty for the application of VACLs to a VLAN on the Cisco Catalyst 6500 Series Switches
Below an example to understand how to configure the switchport capture feature.
Example
Suppose that you want classify the http and https traffic between clients on vlan100 / vlan200 and ServerA / ServerB on vlan10.
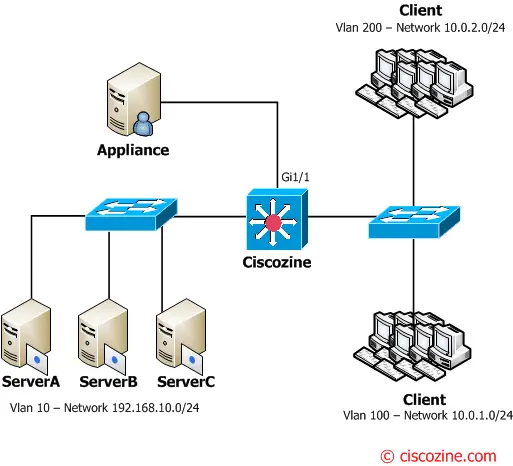
The steps are:
- Define the interesting traffic to be caputured and sent to analysis
- Define an ACL to map all other traffic
- Define the VLAN access map
- Apply the VLAN access map to the appropriate VLANs
- Configure the Capture Port
- Verify the configuration
1. Define the interesting traffic to be caputured and sent to analysis
Ciscozine(config)#ip access-list extended Traffic-to-server Ciscozine(config-ext-nacl)#permit tcp 10.0.1.0 0.0.0.255 host 192.168.10.100 eq 80 443 Ciscozine(config-ext-nacl)#permit tcp 10.0.1.0 0.0.0.255 host 192.168.10.101 eq 80 443 Ciscozine(config-ext-nacl)#permit tcp 10.0.2.0 0.0.0.255 host 192.168.10.100 eq 80 443 Ciscozine(config-ext-nacl)#permit tcp 10.0.2.0 0.0.0.255 host 192.168.10.101 eq 80 443 Ciscozine(config-ext-nacl)#permit tcp host host 192.168.10.100 eq 80 443 tcp 10.0.1.0 0.0.0.255 Ciscozine(config-ext-nacl)#permit tcp host host 192.168.10.101 eq 80 443 tcp 10.0.1.0 0.0.0.255 Ciscozine(config-ext-nacl)#permit tcp host host 192.168.10.100 eq 80 443 tcp 10.0.2.0 0.0.0.255 Ciscozine(config-ext-nacl)#permit tcp host host 192.168.10.101 eq 80 444 tcp 10.0.2.0 0.0.0.255
Remember: You must define the ‘back’ ACL. For instance, if you want capture all the http/https flows between vlan100 and ServerA, it isn’t sufficient the entry:
permit tcp 10.0.1.0 0.0.0.255 host 192.168.10.100 eq 80 443
Indeed, you must define the “back” ACL:
permit tcp host 192.168.10.100 eq 80 443 10.0.1.0 0.0.0.255
2. Define an ACL to map all other traffic
Ciscozine(config)#ip access-list extended ALL_TRAFFIC Ciscozine(config-ext-nacl)#permit ip any any
3. Define the VLAN access map
In this step you must define what traffic must be copied/forwarded
Ciscozine(config)#vlan access-map Traffic-to-server-map 10 Ciscozine(config-access-map)#match ip address Traffic-to-server Ciscozine(config-access-map)#action forward capture
and what traffic must be only forwarded
Ciscozine(config)#vlan access-map Traffic-to-server-map 20 Ciscozine(config-access-map)#match ip address ALL_TRAFFIC Ciscozine(config-access-map)#action forward
4. Apply the VLAN access map to the appropriate VLANs
Ciscozine(config)#vlan filter Traffic-to-server-map vlan-list 10
5. Configure the Capture Port
Ciscozine(config)#int Gi1/1 Ciscozine(config-if)#switchport capture allowed vlan 10 Ciscozine(config-if)#switchport capture
To verify the configuration, you can use these two commands:
show vlan access-map: Displays the contents of the VLAN Access Maps.
Ciscozine#show vlan access-map HTTP_UDP_MAP Vlan access-map "HTTP_UDP_MAP" 10 match: ip address HTTP_UDP_TRAFFIC action: forward capture Vlan access-map "HTTP_UDP_MAP" 20 match: ip address ALL_TRAFFIC action: forward
show vlan filter: Displays information about the VLAN Filters.
Ciscozine#show vlan filter VLAN Map HTTP_UDP_MAP: Configured on VLANs: 10 Active on VLANs: 10
Remember:
- VACLs have an implicit deny at the end of the map; a packet is denied if it does not match any ACL entry, and at least one ACL is configured for the packet type.
- If an empty or undefined ACL is specified in a VACL, any packets will match the ACL, and the associated action is taken.
- To find out if your switch supports this feature take a look at the Cisco Catalyst Switch Guide.
The step #4 and #5 can be changed into:
Ciscozine(config)#vlan filter Traffic-to-server-map vlan-list 100,200 Ciscozine(config)#int Gi1/1 Ciscozine(config-if)#switchport capture allowed vlan 100,200 Ciscozine(config-if)#switchport capture
References:

Really neat – but you know whats cooler – theres Wireshark to do all your pcap captures and analysis right ON the Catalyst 4500 switch itself – no need to span or redirect anything
The switch guide says the 4500 is supported, however I do not have the switchport capture command available. Running cat4500e-universalk9.SPA.03.05.03.E.152-1.E3.bin. with a Sup7-E. Is this supported or is the command setup different on the 4500
From this guide, Cisco says that the switchport capture is supported on 4500. I can’t help you because I have never configured this feature on this device.
Looks like a built-in TAP solution with filter. It is amazing. Thank you for sharing this.