In a typical MAC flooding attack, a switch is flooded with packets, each containing different source MAC addresses. The intention is to consume the limited memory set aside in the switch to store the MAC address-to-physical port translation table.
The result of this attack causes the switch to enter a state called failopen mode, in which all incoming packets are broadcast out on all ports (as with a hub), instead of just down the correct port as per normal operation. A malicious user could then use a packet sniffer running in promiscuous mode to capture sensitive data from other computers, which would not be accessible were the switch operating normally.
Cisco gives you an opportunity to set up protection against this attack with limiting and/or hardwiring some MAC addresses to a dedicated port.
Understand the MAC flooding attack
Suppose to have a switch with 3 PC: PC A, PC B and PC C; in normal situation, when PC A sends a packet to PC B, PC C does not view packet sent between PC A and PC B.
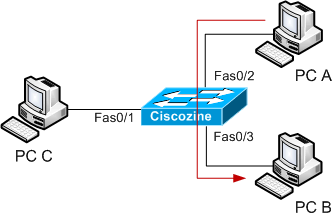
This because the 3 PC are connected to a switch and NOT to a hub.
Under MAC flooding attack, the switch behaviour is different. During the MAC flooding attack, the attacker (in this instance PC C) floods the switch with packets, each with different source MAC address.
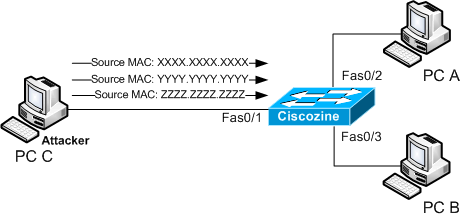
If the Content Addressable Memory (the memory where the MAC addresses are stored) is full, the switch works like an hub; so, if the PC A sends a packet to PC B, the packet will be received to PC C too.
Protecting against MAC flooding attack
Cisco has implemented a feature, called switchport port-security, to protect against this type of attack. You can use the port security feature to restrict input to an interface by limiting and identifying MAC addresses of the stations allowed to access the port.
There are three types of secure MAC addresses:
-
Static secure MAC addresses: These are manually configured by using the switchport port-security mac-address mac-address interface configuration command, stored in the address table, and added to the switch running configuration.
-
Dynamic secure MAC addresses: These are dynamically learned, stored only in the address table, and removed when the switch restarts.
-
Sticky secure MAC addresses: These can be dynamically learned or manually configured, stored in the address table, and added to the running configuration. If these addresses are saved in the configuration file, the interface does not need to dynamically relearn them when the switch restarts.
Remember: A secure port can have from 1 to 132 associated secure addresses. The total number of available secure addresses on the switch is 1024.
When the maximum number of secure MAC addresses have been added to the address table and a station whose MAC address is not in the address table attempts to access the interface a security violation occurs.
The switch can react to a security violation in three different ways:
-
protect: When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. You are not notified that a security violation has occurred.
-
restrict: When the number of secure MAC addresses reaches the limit allowed on the port, packets with unknown source addresses are dropped until you remove a sufficient number of secure MAC addresses or increase the number of maximum allowable addresses. In this mode, you are notified that a security violation has occurred. Specifically, an SNMP trap is sent, a syslog message is logged, and the violation counter increments.
-
shutdown: In this mode, a port security violation causes the interface to immediately become error-disabled, and turns off the port LED. It also sends an SNMP trap, logs a syslog message, and increments the violation counter. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command, or you can manually re-enable it by entering the shutdown and no shutdown interface configuration commands. This is the default mode.
Example: Limit to ten MAC addresses, two of which are statics (aaaa.aaaa.aaaa, bbbb.bbbb.bbbb), on FastEthernet 0/1 port. The violation required is “restricted”.
Ciscozine# conf t Ciscozine(config)# interface fastethernet0/1 Ciscozine(config-if)# switchport mode access Ciscozine(config-if)# switchport port-security Ciscozine(config-if)# switchport port-security maximum 10 Ciscozine(config-if)# switchport port-security violation restrict Ciscozine(config-if)# switchport port-security mac-address aaaa.aaaa.aaaa Ciscozine(config-if)# switchport port-security mac-address bbbb.bbbb.bbbb
switchport mode access: The port-security works only on access port, so define it.
switchport port-security: Enable port security on the interface.
switchport port-security maximum 10: Sets the maximum number of secure MAC addresses for the interface to 10.
switchport port-security violation restrict: It defines to “restrict” the violation mode.
switchport port-security mac-address aaaa.aaaa.aaaa: Define the static MAC address; remember that if you configure fewer secure MAC addresses than the maximum, the remaining MAC addresses are dynamically learned.
Useful commands to displaying traffic control status and configuration are:
-
show interfaces [interface-id] switchport: Displays the administrative and operational status of all switching (nonrouting) ports or the specified port, including port blocking and port protection settings.
-
show port-security [interface interface-id]: Displays port security settings for the switch or for the specified interface, including the maximum allowed number of secure MAC addresses for each interface, the number of secure MAC addresses on the interface, the number of security violations that have occurred, and the violation mode.
-
show port-security [interface interface-id] address: Displays all secure MAC addresses configured on all switch interfaces or on a specified interface with aging information for each address.
Remember: you can enable port security on a interface only if the port is not configured as one of these:
- Trunk ports: If you try to enable port security on a trunk port, an error message appears, and port security is not enabled. If you try to change the mode of a secure port to trunk, the port mode is not changed.
- Dynamic port: A port in dynamic mode can negotiate with its neighbor to become a trunk port. If you try to enable port security on a dynamic port, an error message appears, and port security is not enabled. If you try to change the mode of a secure port to dynamic, the port mode is not changed.
- Dynamic-access port: If you try to enable port security on a dynamic-access (VLAN Query Protocol [VQP]) port, an error message appears, and port security is not enabled. If you try to change a secure port to dynamic VLAN assignment, an error message appears, and the VLAN configuration is not changed.
- EtherChannel porT: Before enabling port security on the port, you must first remove it from the EtherChannel. If you try to enable port security on an EtherChannel or on an active port in an EtherChannel, an error message appears, and port security is not enabled. If you enable port security on a not-yet active port of an EtherChannel, the port does not join the EtherChannel.
- 802.1X port: You cannot configure an 802.1X port as a secure port. If you try to enable port security on an 802.1X port, an error message appears, and port security is not enabled. If you try to change a secure port to an 802.1X port, an error message appears, and the 802.1X settings are not changed.
- Switch Port Analyzer (SPAN) destination port: You can enable port security on a port that is a SPAN destination port; however, port security is disabled until the port is removed as a SPAN destination. You can enable port security on a SPAN source port.
References:

Does my mac adresse change if I upgrade my computer with some other hardware? For example change the graphic card?
you can hide ur MAC address and show a fake MAC address by using third party tool
if there are duplicate mac addresses in diffrent broad cast domain, but in one interface router onstick, what will happen?? how it could be ??
Hi all,
To configure the number of packets which can be transmitted in a second, by using the following command.
mac-flood-guard PORTS
<1-6000>
Mode
Bridge
Description
Limits the number of packets which can be transmitted
to the port for 1 second.
Can anyone help me here which value we can choose?
I do not know the “mac-flood-guard” command (is it CatOS?); however there isn’t a default value but it depends by network, type of device connected to this port and other variables.. My suggestion is try with a value and tune it.