In a previous article, I explained what is and how it works DMVPN technology. In this article you see how to configure DMVPN phase3. This phase allows spokes to build a spoke-to-spoke tunnel and to overcomes the phase2 restriction using NHRP traffic indication messages from the hub to signal to the spokes that a better path exists to reach the target network.
The phase3 configuration is based by 4 steps:
- Define Tunnel interface (mandatory)
- Define NHRP (mandatory)
- Define EIGRP Process (mandatory)
- Define IPSEC Profile (optional)
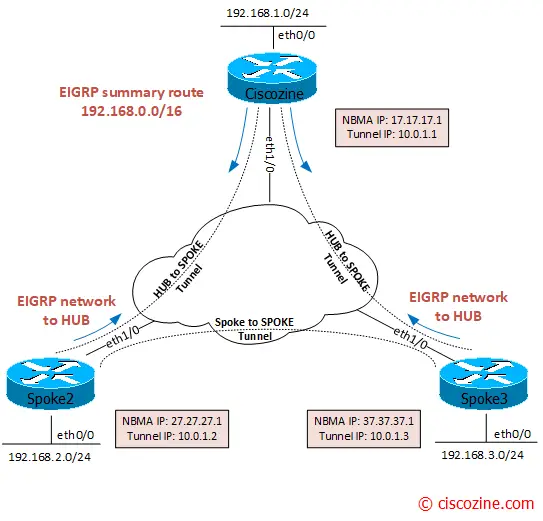
In this example, there are 3 routers: one hub (Ciscozine) and two spokes. The IP address are:
Ciscozine (HUB)
- NBMA IP: 17.17.17.1 (outside ip address) – Eth1/0
- Tunnel IP: 10.0.1.1/24 – Tunnel1
- Network: 192.168.1.0/24 – Eth0/0
Spoke1:
- NBMA IP: 27.27.27.2 (outside ip address) – Eth1/0
- Tunnel IP: 10.0.1.2/24 – Tunnel1
- Network: 192.168.2.0/24 – Eth0/0
Spoke2:
- NBMA IP: 37.37.37.3 (outside ip address) – Eth1/0
- Tunnel IP: 10.0.1.3/24 – Tunnel1
- Network: 192.168.3.0/24 – Eth0/0
Let’s start with the configuration :)
1. Define Tunnel interface
Allow a single GRE interface to support multiple tunnels, simplifying the size and complexity of the configuration.
HUB
interface Tunnel1 description DMVPN-HUB ip address 10.0.1.1 255.255.255.0 ! IP address of the tunnel ip mtu 1400 ip tcp adjust-mss 1360 tunnel source Ethernet1/0 ! The tunnel source is the "outside" interface tunnel mode gre multipoint ! The tunnel type: multipoint GRE tunnel key 101
Spoke2
interface Tunnel1 description DMVPN-SPOKE2 ip address 10.0.1.2 255.255.255.0 ! IP address of the tunnel ip mtu 1400 ip tcp adjust-mss 1360 tunnel source Ethernet1/0 ! The tunnel source is the "outside" interface tunnel mode gre multipoint ! The tunnel type: multipoint GRE tunnel key 101
Spoke3
interface Tunnel1 description DMVPN-SPOKE2 ip address 10.0.1.3 255.255.255.0 ! IP address of the tunnel ip mtu 1400 ip tcp adjust-mss 1360 tunnel source Ethernet1/0 ! The tunnel source is the "outside" interface tunnel mode gre multipoint ! The tunnel type: multipoint GRE tunnel key 101
Note: The MTU is set to 1400bytes due to GRE and IPSEC overhead, while the maximum TCP MSS is 40 bytes lower than the MTU (20 bytes IP header + 20 bytes TCP header).
Below the IPv4 packet details:
New IPv4 Header (Tunnel Mode): 20 bytes
SPI (ESP Header): 4 bytes
Sequence (ESP Header): 4 bytes
ESP-AES (IV): 16 bytes
New IPv4 Header (GRE): 20 bytes
GRE Header + Tunnel Key: 8 bytes
Original Data Packet: 1400 bytes
ESP Pad (ESP-AES): 10 bytes
Pad length (ESP Trailer): 1 byte
Next Header (ESP Trailer): 1 byte
ESP-SHA-256-HMAC ICV (ESP Trailer): 16 bytes
Total IPSec Packet Size: 1500 bytes
Remember: The tunnel key-id is used as a form of weak security to prevent improper configuration or injection of packets from a foreign source. The key must be the same in all tunnels.
2. Define NHRP
Allow spokes to be deployed with dynamically assigned public IP addresses (i.e., behind an ISP’s router). The hub maintains an NHRP database of the public interface addresses of the each spoke. Each spoke registers its real address when it boots; when it needs to build direct tunnels with other spokes, it queries the NHRP database for real addresses of the destination spokes.
HUB
interface Tunnel1 ip nhrp authentication CiscoPWD ! NHRP authentication key ip nhrp map multicast dynamic ip nhrp network-id 101 ! NHRP identifier ip nhrp holdtime 300 ! Seconds that NHRP NBMA addresses are advertised as valid in positive NHRP responses ip nhrp redirect ! Mandatory to enable DMVPN phase3 on the hub router
Note: The “ip nhrp map multicast dynamic” command allows NHRP to automatically add spoke routers to the multicast NHRP mappings when these spoke routers initiate the mGRE tunnel and register their unicast NHRP mappings. This is needed to enable dynamic routing protocols to work over the mGRE tunnels between the hub and spokes.
Spoke2 / Spoke3
interface Tunnel1 ip nhrp authentication CiscoPWD ! NHRP authentication key ip nhrp map 10.0.1.1 17.17.17.1 ip nhrp map multicast 17.17.17.1 ! Enable to receive multicast or broadcast packets ip nhrp network-id 101 ! NHRP identifier ip nhrp holdtime 300 ! Seconds that NHRP NBMA addresses are advertised as valid in positive NHRP responses ip nhrp nhs 10.0.1.1 ip nhrp shortcut ! Mandatory to enable DMVPN phase3 on the spoke router
The command “ip nhrp map 10.0.1.1 17.17.17.1” configure a static mapping IP-to-NBMA of the HUB router, while the command “ip nhrp nhs 10.0.1.1” define the ip address of the next-hop server (hub). These commands are required on spokes routers.
Remember: The authentication string, the holdtime and network-id must be the same in all tunnels.
3. Define EIGRP Process
Learn networks between hub and spokes.
The key chain is used to authenticate EIGRP process; obviously, it must be the same on all routers.
HUB – Spoke1 – Spoke2
key chain DMVPN key 1 key-string eigrp-Ciscozine
HUB
router eigrp 100 network 10.0.1.0 0.0.0.255 ! Used for neighborship network 192.168.1.0 ! Announce the 192.168.1.0/24 network passive-interface default no passive-interface Tunnel1 no passive-interface Ethernet0/0 interface Tunnel1 ip authentication mode eigrp 100 md5 ! Enable MD5 authentication process ip authentication key-chain eigrp 100 DMVPN ! Enable authentication process using DMVPN key chain ip summary-address eigrp 100 192.168.0.0 255.255.0.0 ! Advertise a summary route
Spoke2
router eigrp 100 network 10.0.1.0 0.0.0.255 ! Used for neighborship network 192.168.2.0 ! Announce the 192.168.2.0/24 network passive-interface default no passive-interface Tunnel1 no passive-interface Ethernet0/0 interface Tunnel1 ip authentication mode eigrp 100 md5 ! Enable MD5 authentication process ip authentication key-chain eigrp 100 DMVPN ! Enable authentication process using DMVPN key chain
Spoke3
router eigrp 100 network 10.0.1.0 0.0.0.255 ! Used for neighborship network 192.168.3.0 ! Announce the 192.168.3.0/24 network passive-interface default no passive-interface Tunnel1 no passive-interface Ethernet0/0 interface Tunnel1 ip authentication mode eigrp 100 md5 ! MD5 authentication process ip authentication key-chain eigrp 100 DMVPN ! Enable authentication process using DMVPN key chain
At the end of this step, the DMVPN is operational and can be used but, my suggestion, it is to complete the DMVPM architecture encrypting and protecting all data with IPSEC.
4. Define IPSEC Profile
The last step (optional) is to protect the mGRE tunnel with IPSEC. To do it, you need to define an isakmp policy/profile and a ipsec transform-set/profile.
HUB / Spoke2 / Spoke3
crypto keyring VPN-KEYRING-WAN pre-shared-key address 0.0.0.0 0.0.0.0 key Ciscozine ! Define the preshared key crypto isakmp policy 10 ! Define the isakmp security settings encr aes hash sha256 authentication pre-share group 5 crypto isakmp profile WAN keyring VPN-KEYRING-WAN match identity address 0.0.0.0 crypto ipsec transform-set TSET esp-aes 256 esp-sha256-hmac ! Define the ipsec security settings mode tunnel crypto ipsec profile IPSEC-PROFILE set transform-set TSET
After that, it is possible to apply the IPSEC profile to the tunnel interface:
Interface Tunnel1 tunnel protection ipsec profile IPSEC-PROFILE
Now the architecture is complete and protected by IPSEC.
And what about troubleshooting commands? Stay tuned, you will learn in the next article :)
References:


Great article. Simple lab but very well explained!
Good job! is very clear to understand
Awesome example. I tried to recreate it in EVE-NG, but the hold-time for the tunnel was too big for eigrp and it started flapping. It fixed when i changed it to 200.
Thank you
Thanks for the suggestion!
You don’t have to use EIGRP; you can use OSPF, as I did. There is a bit of a gotcha with OSPF: I could only make it work by using “ip ospf network broadcast” or “ip ospf network point-to-multipoint” on the tunnel interfaces at hub and spokes. If you just leave it as default, the OSPF adjacency will keep coming up and going down repeatedly.