Usually when we admin a network, we need to know what are the protocols used more frequently, and why not, discover if someone are using improper P2P software; so we can use SPAN.
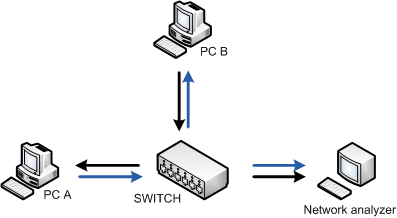
The Switched Port Analyzer (SPAN) feature, which is sometimes called port mirroring or port monitoring, selects network traffic for analysis by a network analyzer. For example, if you want to capture Ethernet traffic that is sent between host A and host B, you must implement SPAN feature.
In this diagram, the sniffer is attached to a port (destination SPAN port) that is configured to receive a copy of every packet sent between host A and host B (source SPAN port). This port is called a SPAN port.
A source port, also called a monitored port, is a switched or routed port that you monitor for network traffic analysis. In a single local SPAN session or RSPAN source session, you can monitor source port traffic, such as received (Rx), transmitted (Tx), or bidirectional (both). The switch supports any number of source ports (up to the maximum number of available ports on the switch) and any number of source VLANs.
A source port has these characteristics:
- It can be any port type, such as EtherChannel, Fast Ethernet, Gigabit Ethernet, and so forth.
- It can be monitored in multiple SPAN sessions.
- It cannot be a destination port.
- Each source port can be configured with a direction (ingress, egress, or both) to monitor. For EtherChannel sources, the monitored direction applies to all physical ports in the group.
- Source ports can be in the same or different VLANs.
- For VLAN SPAN sources, all active ports in the source VLAN are included as source ports.
Each local SPAN session or RSPAN destination session must have a destination port (also called a monitoring port) that receives a copy of traffic from the source ports and VLANs.
A destination port has these characteristics:
- A destination port must reside on the same switch as the source port (for a local SPAN session).
- A destination port can be any Ethernet physical port.
- A destination port can participate in only one SPAN session at a time. A destination port in one SPAN session cannot be a destination port for a second SPAN session.
- A destination port cannot be a source port.
- A destination port cannot be an EtherChannel group.
- A destination port can be a physical port that is assigned to an EtherChannel group, even if the EtherChannel group has been specified as a SPAN source. The port is removed from the group while it is configured as a SPAN destination port.
- The port does not transmit any traffic except that traffic required for the SPAN session unless learning is enabled. If learning is enabled, the port also transmits traffic directed to hosts that have been learned on the destination port.
- The state of the destination port is up/down by design. The interface shows the port in this state in order to make it evident that the port is currently not usable as a production port.
- If ingress traffic forwarding is enabled for a network security device. The destination port forwards traffic at Layer 2.
- A destination port does not participate in spanning tree while the SPAN session is active.
- When it is a destination port, it does not participate in any of the Layer 2 protocols (STP, VTP, CDP, DTP, PagP).
- A destination port that belongs to a source VLAN of any SPAN session is excluded from the source list and is not monitored.
- A destination port receives copies of sent and received traffic for all monitored source ports. If a destination port is oversubscribed, it can become congested. This congestion can affect traffic forwarding on one or more of the source ports.
For example, if I want monitor traffic from/to fastethernet 0/1 (source port) using fastethernet0/3 (destination port) on my Catalyst 2950, the configuration is:
SW2950#configure terminal SW2950(config)# SW2950(config)#monitor session 1 source interface fastethernet 0/1 SW2950(config)#monitor session 1 destination interface fastethernet 0/3 SW2950(config)# SW2950#show monitor session 1 Session 1 --------- Source Ports: RX Only: None TX Only: None Both: Fa0/1 Destination Ports: Fa0/3 SW2950#
This configuration works also for the Catalyst 2940, 2955, 2960, 2970, 3550, 3560, 3560-E, 3750 and 3750-E Series Switches. Instead if I use a Catalyst 2900XL/3500XL the configuration is quite different:
SW2900XL(config)#interface fastethernet 0/3 SW2900XL(config-if)#port monitor fastethernet 0/1
Sometimes source ports are not located on the same switch as the destination port; in these situations is needed use an advanced SPAN feature: RSPAN or ERSPAN.
Remote SPAN (RSPAN) allows you to monitor source ports that are spread all over a switched network, not only locally on a switch with SPAN. The functionality works exactly as a regular SPAN session. The traffic that is monitored by SPAN is not directly copied to the destination port, but flooded into a special RSPAN VLAN. The destination port can then be located anywhere in this RSPAN VLAN. There can even be several destination ports.
RSPAN session cannot cross any Layer 3 device as RSPAN is a LAN (Layer 2) feature. In order to monitor traffic across a WAN or different networks, use Encapsulated Remote SwitchPort Analyser (ERSPAN).
The ERSPAN feature supports source ports, source VLANs, and destination ports on different switches, which provides remote monitoring of multiple switches across your network.
ERSPAN consists of an ERSPAN source session, routable ERSPAN GRE-encapsulated traffic, and an ERSPAN destination session. You separately configure ERSPAN source sessions and destination sessions on different switches.
Catalyst Switches That Support SPAN, RSPAN, and ERSPAN:
| Catalyst Switches | SPAN Support | RSPAN Support | ERSPAN Support |
| Catalyst Express 500 Series | Yes | No | No |
| Catalyst 6500/6000 Series | Yes | Yes | Yes Supervisor 720 with PFC3B or PFC3BXL running Cisco IOS Software Release 12.2(18)SXE or later. Supervisor 720 with PFC3A that has hardware version 3.2 or later and running Cisco IOS Software Release 12.2(18)SXE or later |
| Catalyst 5500/5000 Series | Yes | No | No |
| Catalyst 4900 Series | Yes | Yes | No |
| Catalyst 4500/4000 Series (includes 4912G) | Yes | Yes | No |
| Catalyst 3750 Metro Series | Yes | Yes | No |
| Catalyst 3750 / 3750E Series | Yes | Yes | No |
| Catalyst 3560 / 3560E Series | Yes | Yes | No |
| Catalyst 3550 Series | Yes | Yes | No |
| Catalyst 3500 XL Series | Yes | No | No |
| Catalyst 2970 Series | Yes | Yes | No |
| Catalyst 2960 Series | Yes | Yes | No |
| Catalyst 2955 Series | Yes | Yes | No |
| Catalyst 2950 Series | Yes | Yes | No |
| Catalyst 2940 Series | Yes | No | No |
| Catalyst 2948G-L3 | No | No | No |
| Catalyst 2948G-L2, 2948G-GE-TX, 2980G-A | Yes | Yes | No |
| Catalyst 2900XL Series | Yes | No | No |
| Catalyst 1900 Series | Yes | No | No |
And now?! Now it is possible analyze the traffic connecting the NIC of your PC (remember to set it to promiscuous mode…) with the SPAN port of your switch.
A good tools to analyze the traffic are:
- Packetyzer: http://sourceforge.net/projects/packetyzer/
Packetyzer provides a Windows user interface for the Ethereal packet capture and dissection library. Ethereal is used by network professionals around the world for troubleshooting, analysis, software and protocol development, and education. Ethereal has all of the standard features expected in a protocol analyzer, and several features not otherwise available. - Wireshark: http://www.wireshark.org/
Wireshark is a free packet sniffer computer application. It is used for network troubleshooting, analysis, software and communications protocol development, and education. The functionality Wireshark provides is very similar to tcpdump, but it has a graphical front-end, and many more information sorting and filtering options. It allows the user to see all traffic being passed over the network (usually an Ethernet network but support is being added for others) by putting the network interface into promiscuous mode. - TCPdump: http://www.tcpdump.org/
Tcpdump is an open source command-line tool for monitoring network traffic. Tcpdump works by capturing and displaying packet headers and matching them against a set of criteria. It understands Boolean search operators and can use host names, IP addresses, network names, and protocols as arguments. - NTOP: http://www.ntop.org
ntop is a network traffic probe that shows the network usage, similar to what the popular top Unix command does. ntop is based on libpcap and it has been written in a portable way in order to virtually run on every Unix platform and on Win32 as well. ntop users can use a a web browser (e.g. netscape) to navigate through ntop (that acts as a web server) traffic information and get a dump of the network status. In the latter case, ntop can be seen as a simple RMON-like agent with an embedded web interface.
References: http://www.cisco.com/…/products_tech_note09186a008015c612.shtml

Good stuff, thanks!
grazie! e’ proprio quello che cercavo! complimenti per il sito, ormai e’ una delle mie homepage!
Hello,
Great article — I just wanted to point out that the Catalyst 2950 does NOT support RSPAN, although the 2950LRE (Long Reach Ethernet) model DOES support RSPAN. You can check using the Cisco Feature Navigator to see what IOS devices provide RSPAN. Thank you.
Hey..great stuff it realy helps new IT guy like me