The Spanning Tree Protocol is an OSI layer-2 protocol that ensures a loop-free topology for any bridged LAN. Spanning tree allows a network design to include spare (redundant) links to provide automatic backup paths if an active link fails, without the danger of bridge loops, or the need for manual enabling/disabling of these backup links. Bridge loops must be avoided because they result in flooding the network.
The Spanning Tree Protocol (STP), is defined in the IEEE Standard 802.1D. As the name suggests, it creates a spanning tree within a mesh network of connected layer-2 bridges (typically Ethernet switches), and disables those links that are not part of the tree, leaving a single active path between any two network nodes.
But what happens if a switch doesn’t receive BPDU in a timely manner or when it doesn’t receive any? In this case the topology must have changed and blocked ports can be unblocked, so a “logical” loop can occur.
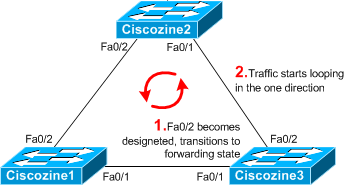
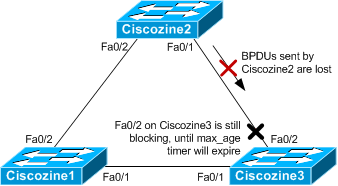
Consider this example in order to illustrate this behavior. Ciscozine1 is the root switch and the fastethernet0/2 of Ciscozine3 is in blocking state. Ciscozine3 does not receive BPDUs from Ciscozine2 due to unidirectional link failure on the link between Ciscozine2 and Ciscozine3.
The STP blocking port on Ciscozine3 transitions to the STP listening state when the max_age timer expires, and then it transitions to the forwarding state in two times the forward_delay time. This situation creates a loop.
To preventing STP forwarding loops, Cisco has implemented two features to detect unexpected BPDU loss: UDLD and loop guard.
Loop guard and Unidirectional Link Detection (UDLD) functionality overlap, partly in the sense that both protect against STP failures caused by unidirectional links. However, these two features differ in functionality and how they approach the problem. This table describes loop guard and UDLD functionality:
| Functionality | Loop Guard | UDLD |
| Configuration | Per-port | Per-port |
| Action granularity | Per-VLAN | Per-port |
| Autorecover | Yes | Yes, with err-disable timeout feature |
| Protection against STP failures caused by unidirectional links | Yes, when enabled on all root and alternate ports in redundant topology | Yes, when enabled on all links in redundant topology |
| Protection against STP failures caused by problems in the software (designated switch does not send BPDU) | Yes | No |
| Protection against miswiring. | No | Yes |
UDLD
UDLD is a Layer 2 protocol that enables devices connected through fiber-optic or twisted-pair Ethernet cables to monitor the physical configuration of the cables and detect when a unidirectional link exists. All connected devices must support UDLD for the protocol to successfully identify and disable unidirectional links. When UDLD detects a unidirectional link, it administratively shuts down the affected port and alerts you.
UDLD supports two modes: normal (the default) and aggressive. In normal mode, UDLD can detect unidirectional links due to misconnected interfaces on fiber-optic connections. In aggressive mode, UDLD can also detect unidirectional links due to one-way traffic on fiber-optic and twisted-pair links and to misconnected interfaces on fiber-optic links.
Normally UDLD is disabled by default; to enable it:
Enable UDLD globally: aggressive mode (on all fiber-optic interfaces)
Ciscozine3# conf t Ciscozine3(config)# udld aggressive
Enable UDLD globally: normal mode (on all fiber-optic interfaces)
Ciscozine3# conf t Ciscozine3(config)# udld normal
Enable UDLD on a interface: aggressive mode
Ciscozine3# conf t Ciscozine3(config)# interface fastethernet0/2 Ciscozine3(config-if)# udld port aggressive
Enable UDLD on a interface: normal mode
Ciscozine3# conf t Ciscozine3(config)# interface fastethernet0/2 Ciscozine3(config-if)# udld port
To verify the UDLD configuration use the command show udld ?
If UDLD notices an unidirectional link, it shutdown the port. To re-enable it use the command udld reset in the privileged EXEC mode.
REMEMBER:
- UDLD is not supported on ATM interfaces.
- A UDLD-capable interface also cannot detect a unidirectional link if it is connected to a UDLD-incapable port of another switch.
- When configuring the mode (normal or aggressive), make sure that the same mode is configured on both sides of the link.
Loop guard
The STP loop guard feature provides additional protection against Layer 2 forwarding loops (STP loops). If BPDUs are not received on a non-designated port, and loop guard is enabled, that port is moved into the STP loop-inconsistent blocking state, instead of the listening / learning / forwarding state.
Enable loop guard globally
Ciscozine3# conf t Ciscozine3(config)# spanning-tree loopguard default
Enable loop guard on a interface
Ciscozine3# conf t Ciscozine3(config)# interface fastethernet0/2 Ciscozine3(config-if)# spanning-tree guard loop
Use the command show spanning-tree ? to check if there are ports in a inconsistent state.
REMEMBER: Once the BPDU is received on a port in a loop-inconsistent STP state, the port transitions into another STP state. According to the received BPDU, this means that the recovery is automatic and intervention is not necessary.
References:

One of the best articles on net, about LoopGuard and UDLD. Thank you very much.
It is clear enoguh.. Thank you.
concepts of loop guard and UDLD with scenario is really well explained. Thank you