In the article vPC aka Virtual PortChannel, I explained how vPC works and the benefits that it gives. However, there is another important feature using HSRP/VRRP protocols in the context of vPC: the Layer2 dual–active peer devices.
What does it mean?
HSRP and VRRP operate in active-active mode from data plane standpoint, as opposed to classical active/standby implementation with STP based network. From a control plane standpoint, active-standby mode still applies for HSRP/VRRP in context of vPC.
A characteristic of the active HSRP/VRRP peer device is that it is the only one to respond to ARP requests for HSRP/VRRP VIP (Virtual IP). ARP response will contain the HSRP/VRRP vMAC which is the same on both vPC peer devices.
The standby HSRP/VRRP vPC peer device just relays the ARP request to active HSRP/VRRP peer device through vPC peer-link
Note: No additional configuration is required to enable active/active HSRP/VRRP.
Example:
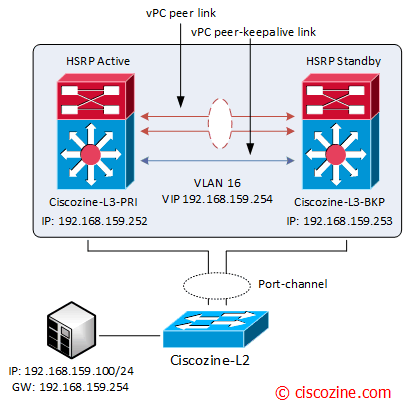
Suppose to have 1 Nexus5K (Ciscozine-L2) conntected to 2 Nexus7K (Ciscozine-L3-PRI and Ciscozine-L3-BKP).
The Layer3 is defined on the Nexus pair (192.168.159.0/24) and the Active HSRP is Ciscozine-L3_PRI.
Below the N7K HSRP configurations (the VPC configuration is omitted):
Ciscozine-L3-PRI
interface Vlan16
no shutdown
description TEST_HSRP
vrf member ciscozine
ip address 192.168.159.252/24
hsrp 16
authentication text C1sc0zin3
preempt delay minimum 300
priority 130
ip 192.168.159.254
Ciscozine-L3-BKP
interface Vlan16
no shutdown
description TEST_HSRP
vrf member ciscozine
ip address 192.168.159.253/24
hsrp 16
authentication text C1sc0zin3
preempt delay minimum 300
priority 110
ip 192.168.159.254
Show output
Ciscozine-L3-PRI# sh hsrp interface vlan 16
Vlan16 - Group 16 (HSRP-V1) (IPv4)
Local state is Active, priority 130 (Cfged 130), may preempt
Forwarding threshold(for vPC), lower: 1 upper: 130
Preemption Delay (Seconds) Minimum:300
Hellotime 3 sec, holdtime 10 sec
Next hello sent in 1.226000 sec(s)
Virtual IP address is 192.168.159.254 (Cfged)
Active router is local
Standby router is 192.168.159.253 , priority 110 expires in 4.297000 sec(s)
Authentication text "C1sc0zin3"
Virtual mac address is 0000.0c07.ac10 (Default MAC)
3397 state changes, last state change 30w0d
IP redundancy name is hsrp-Vlan16-16 (default)
Ciscozine-L3-PRI#
Ciscozine-L3-BKP# sh hsrp interface vlan 16
Vlan16 - Group 16 (HSRP-V1) (IPv4)
Local state is Standby, priority 110 (Cfged 110), may preempt
Forwarding threshold(for vPC), lower: 1 upper: 110
Preemption Delay (Seconds) Minimum:300
Hellotime 250 msec, holdtime 750 msec
Next hello sent in 0.179000 sec(s)
Virtual IP address is 192.168.159.254 (Cfged)
Active router is 192.168.159.252, priority 130 expires in 0.716000 sec(s)
Standby router is local
Authentication text "C1sc0zin3"
Virtual mac address is 0000.0c07.ac10 (Default MAC)
7 state changes, last state change 30w0d
IP redundancy name is hsrp-Vlan16-16 (default)
Ciscozine-L3-BKP#
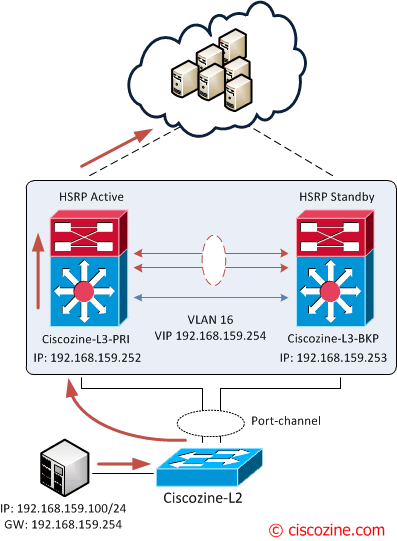
Suppose that a packet is sent from 192.168.159.100 to a server in the cloud. Two events can occur:
1. The packet reaches Ciscozine-L3-PRI (the active HSRP), than it is forwarded to the cloud.
Ciscozine-L3-PRI# show ip arp vrf ciscozine | i 192.168.159.254 192.168.159.254 - 0000.0c07.ac10 Vlan16 Ciscozine-L3-PRI#
Ciscozine-L3-PRI# show mac address-table address 0000.0c07.ac10
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link
VLAN MAC Address Type age Secure NTFY Ports/SWID.SSID.LID
---------+-----------------+--------+---------+------+----+------------------
G 16 0000.0c07.ac10 static - F F sup-eth1(R)
Ciscozine-L3-PRI#
Note: the “0000.0c07.ac10” is the vlan16 virtual mac address.
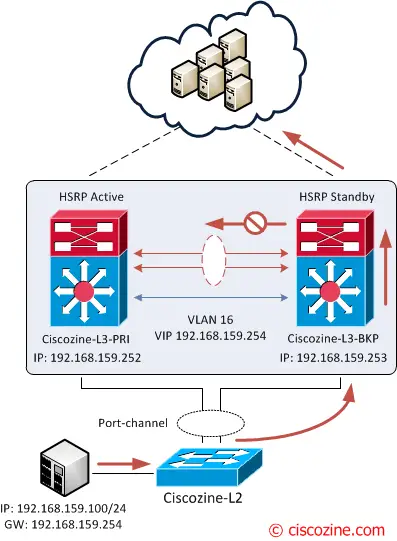
2. The packet reaches Ciscozine-L3-BKP (the standby HSRP), than it is forwarded to the cloud! Why does the packet received by the Ciscozine-L3-BKP is sent to the cloud and not to the virtual-link?
This is implemented by imposing the G bit in the MAC address table (thanks to the vPC feature), that indicates that this traffic is meant to be routed. This is the reason why the HSRP with vPC works as active/active!
Ciscozine-L3-BKP# show ip arp vrf ciscozine | i 192.168.159.254 192.168.159.254 00:00:42 0000.0c07.ac10 Vlan16 Ciscozine-L3-BKP#
Ciscozine-L3-BKP# show mac address-table address 0000.0c07.ac10
Legend:
* - primary entry, G - Gateway MAC, (R) - Routed MAC, O - Overlay MAC
age - seconds since last seen,+ - primary entry using vPC Peer-Link
VLAN MAC Address Type age Secure NTFY Ports/SWID.SSID.LID
---------+-----------------+--------+---------+------+----+------------------
G 16 0000.0c07.ac10 static - F F vPC Peer-Link(R)
Ciscozine-L3-BKP#
Note: The same behaviour occurs using VRRP.
References: http://www.cisco.com/…/vpc_best_practices_design_guide.pdf

First diagram seems wrong, wrong arrow.
hi Fabio, I am testing your scenario but I have a few questions if you kindly answer to them:
1.-Is the G bit imposed by the Ciscozine-L2 switch thanks to the VPC feature?
2.-Do I need to enable VPC Peer-Gateway to make it work?. If it so, is the right command to verify the Peer-Gateway enabled the SHOW VPC so the output for validation is the next?
DC-N9K# show vpc
Legend:
(*) – local vPC is down, forwarding via vPC peer-link
vPC domain id : 100
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : success
vPC role : primary, operational secondary
Number of vPCs configured : 4
Peer Gateway : Enabled *******************THIS ONE******
Hi,
1. Yes, the G bit is imposed thanks to the VPC technology
2. no, the VPN Peer-gateway is another feauter used with some storage system; check this link https://supportforums.cisco.com/t5/lan-switching-and-routing/vpc-peer-gateway/td-p/2726210
Hello
This traffic that can be sent by both Nexus Active and Nexus Standby, can generate asymmetric traffic in the network? I want to say if there is a Firewall on top of the Nexus devices, can I receive tcp non syn?
Regards,
Hi there,
Thank you for the post.
There’s interesting case I’ve come up with after reading this post.
Let’s say Ciscozine-L2 sends some traffic towards servers in the cloud. Packets took path thru the link going to Ciscozine-L3-BKP. Since we have HSRP active-active it can and it will forward those packets if it has route to the destination. Imagine that Ciscozine-L3-BKP lost or doesn’t have a route to the destination to which Ciscozine-L2 sent packtes to. What is going to happen in this case? Will traffic be backholed or it will be forwarded via vPC peer-link and routed to the destination according to the routing information present on the Ciscozine-L3-PRI.
P.S.: I understand that there’re workarounds for such scenario as I described such as to use separated L3 link between vpc pair or to have designated point-to-point SVI on allowed only on the peer-link to establish routing adjacency.
Thanks for reply.
Hello Fabio,
Fanatic article! Quick question. Are the vPC member ports connecting to Ciscozine-L2 also in an LACP ether-channel bundle?
hi i follow the instruction but it gave me that “Local state is Initial(Interface Down)” even though i do no shut for all interfaces
In my opinion, the traffic will be forwarded via vPC.
But you need to check CEF table.