As you see in the article “Implementing High Availability with HSRP“, it is quite simple configure Hot Standby Router Protocol.
Some cases require a custom configuration, using priority, track, preempt etc…and these are:
- The standby preempt interface configuration command allows the router to become the active router when its priority is higher than all other HSRP-configured routers in this Hot Standby group. The configurations of both routers include this command so that each router can be the standby router for the other router. If you do not use the standby preempt command in the configuration for a router, that router cannot become the active router.
- The standby priority interface configuration command sets the router’s HSRP priority (the default priority is 100).
- The standby timers interface configuration command sets the interval in seconds between hello messages (called the hello time) to five seconds and sets the duration in seconds that a router waits before it declares the active router to be down (called the hold time) to eight seconds. (The defaults are three and 10 seconds, respectively.) If you decide to modify the default values, you must configure each router to use the same hello time and hold time.
- The standby track command allows you to specify another interface on the router for the HSRP process to monitor in order to alter the HSRP priority for a given group. If the line protocol of the specified interface goes down, the HSRP priority is reduced. This means that another HSRP router with higher priority can become the active router if that router has standby preempt enabled.
- The standby authentication interface configuration command establishes an authentication string whose value is an unencrypted eight-character string that is incorporated in each HSRP multicast message. This command is optional. If you choose to use it, each HSRP-configured router in the group should use the same string so that each router can authenticate the source of the HSRP messages that it receives.
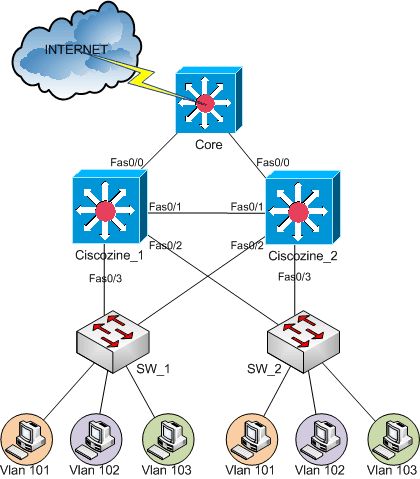
Suppose to have this physical configuration:
Partial configuration of Ciscozine_1 layer3 switch:
Ciscozine_1# ip routing interface FastEthernet0/0 switchport trunk encapsulation dot1q switchport mode trunk interface FastEthernet0/1 switchport trunk encapsulation dot1q switchport mode trunk interface FastEthernet0/2 switchport trunk encapsulation dot1q switchport mode trunk interface FastEthernet0/3 switchport trunk encapsulation dot1q switchport mode trunk interface Vlan101 ip address 172.16.101.2 255.255.255.0 standby 1 ip 172.16.101.1 standby 1 priority 150 standby 1 preempt standby 1 track FastEthernet0/3 55 standby 1 authentication C3s_101 no shutdown interface Vlan102 ip address 172.16.102.2 255.255.255.0 standby 2 ip 172.16.102.1 standby 2 preempt standby 2 track FastEthernet0/3 standby 2 authentication C3s_102 no shutdown interface Vlan103 ip address 172.16.103.2 255.255.255.0 standby 3 ip 172.16.103.1 standby 3 priority 150 standby 3 preempt standby 3 track FastEthernet0/3 50 standby 3 authentication C3s_103 no shutdown
Partial configuration of Ciscozine_2 layer3 switch:
Ciscozine_2# ip routing interface FastEthernet0/0 switchport trunk encapsulation dot1q switchport mode trunk interface FastEthernet0/1 switchport trunk encapsulation dot1q switchport mode trunk interface FastEthernet0/2 switchport trunk encapsulation dot1q switchport mode trunk interface FastEthernet0/3 switchport trunk encapsulation dot1q switchport mode trunk interface Vlan101 ip address 172.16.101.3 255.255.255.0 standby 1 ip 172.16.101.1 standby 1 preempt standby 1 track FastEthernet0/3 standby 1 authentication C3s_101 no shutdown interface Vlan102 ip address 172.16.102.3 255.255.255.0 standby 2 ip 172.16.102.1 standby 2 priority 150 standby 2 preempt standby 2 track FastEthernet0/3 60 standby 2 authentication C3s_102 no shutdown interface Vlan103 ip address 172.16.103.3 255.255.255.0 standby 3 ip 172.16.103.1 standby 3 preempt standby 3 track FastEthernet0/3 standby 3 authentication C3s_103 no shutdown
The commands
switchport trunk encapsulation dot1q switchport mode trunk enable the dot1q trunk between the switches.
The command
ip routing enable the routing on the layer3 switches.
Ciscozine_1 layer3 switch is the primary device for VLAN 101 and VLAN 103 and the backup device for VLAN 102; Ciscozine_2 layer3 switch is the primary device for VLAN 102 and the backup device for VLAN101 and VLAN 103. This type of configuration permits to balance the network load.
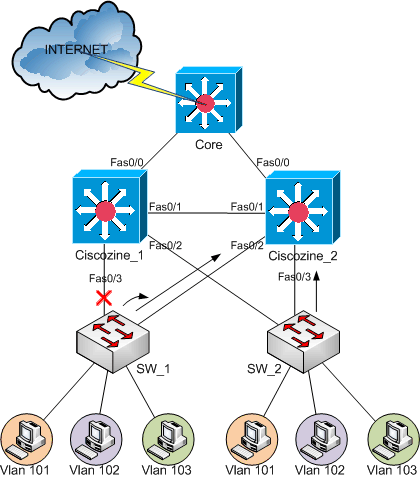
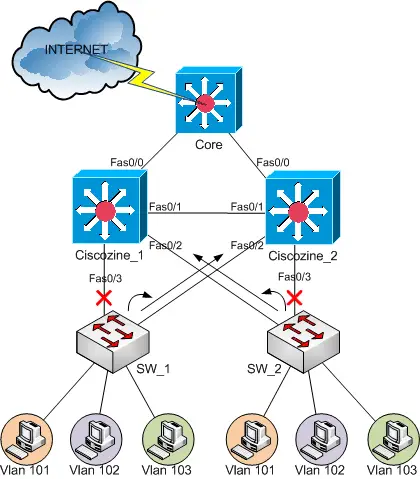
If there is a failure of FastEthernet 0/3 on the primary device, the backup device will be the new primary device, unless FastEthernet 0/3 on the backup device has also failed or the FastEthernet0/3 on the primary device will active again. This behaviour is drawn below.
If Ciscozine_1 FastEthernet0/3 is down, the Ciscozine_2 will be the active router for VLAN 101 and VLAN 103.
If the Ciscozine_1 FastEthernet0/3 and Ciscozine_2 FastEthernet0/3 are down, the active router for VLAN 101 and VLAN 103 will be Ciscozine_1.
Now look at this configuration:
| Ciscozine_1 | Ciscozine_2 | |
| interface Vlan103 | interface Vlan103 | |
| ip address 172.16.103.2 255.255.255.0 | ip address 172.16.103.3 255.255.255.0 | |
| standby 3 ip 172.16.103.1 | 1 | standby 3 ip 172.16.103.1 |
| standby 3 priority 150 | 2 | |
| standby 3 preempt | 3 | standby 3 preempt |
| standby 3 track FastEthernet0/3 50 | 4 | standby 3 track FastEthernet0/3 |
| standby 3 authentication Cés_103 | 5 | standby 3 authentication Cés_103 |
In this instance:
- the standby ip address is 172.16.103.1
- the HSRP prefers the router with higher priority and, if it is equal, it prefers the highter IP address. Ciscozine_1 is the active router because it has a priority of 150 while Ciscozine_2 has default priority of 100.
- bofh switches have preempt to become the active router when its priority is higher than all other HSRP-configured routers in this Hot Standby group.
- Interface tracking enables the priority of a standby group router to be automatically adjusted based on the availability of that router’s interfaces. When a tracked interface becomes unavailable, the HSRP priority of the router is decreased. When properly configured, the HSRP tracking feature ensures that a router with an unavailable key interface relinquishes the active router role. If the Ciscozine_1 FastEthernet0/3 is down, the HSRP priority is decremented of 50 and so the priority will be 100 (150-50). Bofh router will be a HSRP priority of 100 and then the Ciscozine_2 will be the active router because it has the higher ip address. If the Ciscozine_2 FastEthernet 0/3 will be down, the priority of Ciscozine_2 will be decremented of 10 (default value) and so the priority will be 90 (100-10). Then the active router will be Ciscozine_1 again!
- the authentication key is C3s_103 and it is sent in clear text. Remember that from the IOS release 12.3(2)T it is possible send the hashed key using MD5.
Similar behavior is applied to VLAN 101 and VLAN 102.

Excellent work!
Please keep up your efforts.
Thank you!
Hi,
I’m not understanding when you say: “If Ciscozine_1 FastEthernet0/3 is down, the Ciscozine_2 will be the active router for VLAN 101 and VLAN 103”.
That’s it true for Layer2 topology but the two cores still communicate through on interface FastEthernet0/1; I think than Layer3 topology doesn’t change. Is it right ?
However the track solution is useful to avoid the packet redirect toward Ciscozine_1 for reach the default gateway.
Best regards,
Iarno Pagliani
Hi,
In nominal situation Ciscozine_1 is the GW for VLAN101 and VLAN103. If Ciscozine_1 Fas0/3 is down, the HSRP of VLAN101 and VLAN 103 is decremented from 150 to 95 (150-55). So Ciscozine_2 (with preempt and priority equal to 100) will be the new gateway for VLAN101 and VLAN103.
To summarize: if a host connected to SW_1 sends a packet to Internet, the packet will pass through Ciscozine_2, Core and Internet.
thanks man..this is what i need
good works….
Really a great effort…Anyone can easily understand the concept at a glance!!
Thanks ….
Dears,
What about Core router, are it configure by HSRP protocol or Ciscozine_1 and Ciscozine_2 configured with HSRP only? Please your reply.
Dears all,
I have problem with ping command from PC to the Core router. The interface Fas0/0 in Cisco_zine router configured with ip address 150.0.0.2; the interface Fas0/0 in Core router configured with ip address 150.0.0.20, both interfaces with subnet mask 255.255.255.0. In Core router I did Interface loopback with ip address 180.0.0.2. When I do ping using VPC simulator to Cisco_zine interface 150.0.0.2, I recieved reply, but when doing ping to Core interface 150.0.0.20 or to loopback 180.0.0.2, I didn’t recieve reply to request. Please I need your help.
Note: both interfaces in Cisco_zine and Core routers I configured:
Core# ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
Cisco_zine# ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0