Like every year, Cisco has released the Midyear Security Report. This paper is written to understand how attackers are evolving their techniques to evade defenses, using stealthy tactics based on agility, speed, adaptation, and even destruction.
New threat intelligence and trend analysis reveal how attackers use stealthy tactics based on agility, speed, adaptation, and even destruction.
During this year, adversaries continue to innovate as they slip into networks undetected and evade security measures:
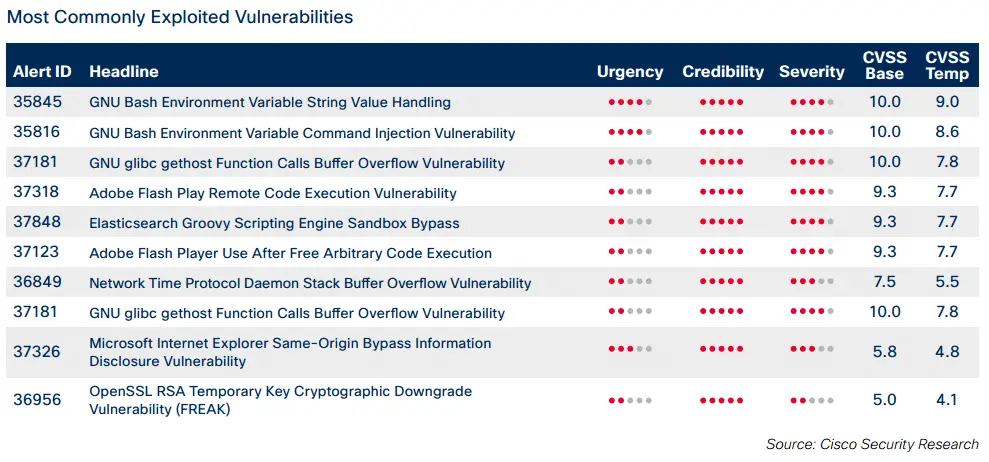
- Exploits of Adobe Flash vulnerabilities are increasing. They are regularly integrated into widely used exploit kits such as Angler and Nuclear.
- Operators of crimeware, like ransomware, are hiring and funding professional development teams to help them make sure their tactics remain profitable.
- Spam volume is increasing in the United States, China, and the Russian Federation, but remained relatively stable in other regions in the first five months of 2015.
- Criminals are turning to the anonymous web network Tor and the Invisible Internet Project (I2P) to relay command-and-control communications while evading detection.
- Malware authors are increasing their use of techniques such as sandbox detection to conceal their presence on networks.
For these reasons, Cisco security experts suggest that change is imminent for the security industry. ” A wave of consolidation and integration is needed to develop innovative, adaptive, and trustworthy security solutions that can reduce time to detection and prevent attacks. In addition, our geopolitical experts provide insight into the importance of cybergovernance for supporting innovation and economic growth in business on the global stage.” the Midyear Security reports.
To get the report: http://www.cisco.com/…/2015-midyear-security-report/index.html
If you want see the top insights from 2015 Cisco Midyear Security Report, watch this video:

Good enlightenment